Photo from ilobby
Photo from ilobby
Originally Posted On: https://www.ilobby.com/blog/visitor-management-compliance
Organizations of all sizes benefit from following compliance and data regulations. It makes your facility and data more secure and creates a positive public image. Even voluntary programs are worthwhile as they improve relations with government organizations and speed up processing times. At the same time, adhering to regulations protects you from legal action, penalties, fines, and recalls. On all counts, innovative compliance software improves profitability and security.
Your facility’s entrances are the first point of vulnerability for many compliance and data governance standards. To that end, visitor management systems (VMS) are a prime opportunity to boost compliance. Most regulations can be incorporated into or enhanced by your visitor management software.
This guide explores the importance of compliance and data governance and how to incorporate them into your facility management platform. This is not legal advice, nor should this article act as a replacement for having your legal team review the specific compliance needs of your organization.
Contents Reduce Compliance Risk Visitor Management Compliance Features Data Governance Compliance Standards & Regulations CCPA CTPAT FISMA FSMA GDPR GLBA & FMA GMP ITAR PCI DSS SOC 2 Type 2
Why You Need to Reduce Compliance Risk
Compliance matters. Unlike standards, which offer guidance and best practices, regulations are enforced. Failure to comply can mean significant fines and heavy penalties. Worst of all, it has a lasting impact on your brand image. But it’s not all doom and gloom.
When you take steps to reduce compliance risks, it speaks volumes about your organization. You are telling the world that this organization cares about the people (and their data) that it interacts with. Proactive compliance doesn’t just avoid penalties; it builds your reputation.
Proactive compliance measures start with familiarizing yourself with the relevant regulations for your industry and organization. GDPR, for example, deals with data protection regulations that extend to nearly every organization with a website – which is pretty much every organization.
While knowledge may be half the battle (Go Joe!), it’s only the beginning. You need to develop smart procedures and tools to comply with relevant regulations. Organizations employ proactive compliance strategies, such as leveraging software that integrates compliance automation.

Visitor Management Compliance
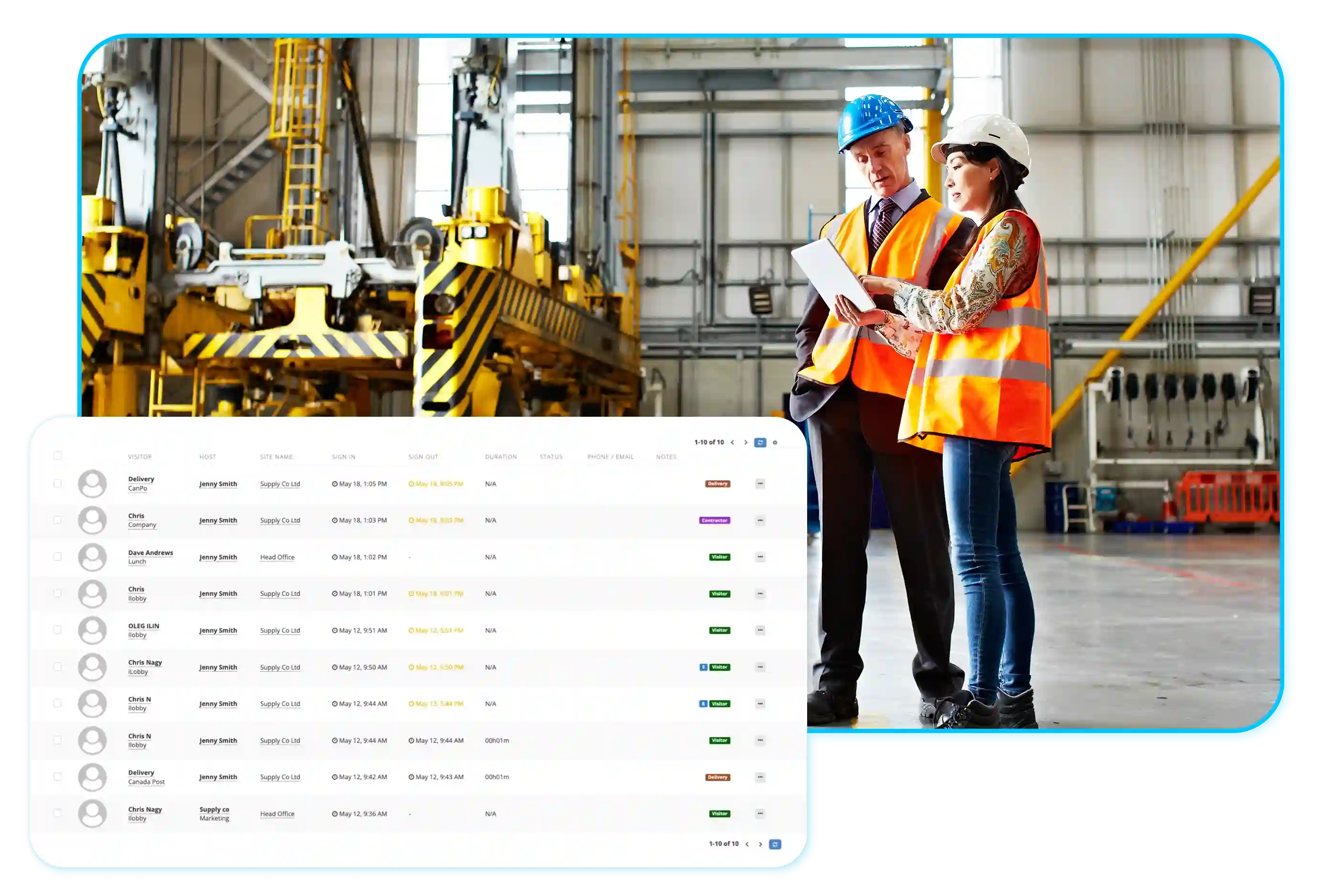
Electronic visitor management platforms can ease specific compliance needs. For example, iLobby workplace management software is officially SOC-compliant, meeting data security compliance regulations.
Managing multiple compliance requirements is complex. Any errors that occur can result in penalties or fines. A cloud-based visitor management system should offer a powerful solution to simplify and integrate processes for streamlined day-to-day use.
Visitor management software incorporates many of the most valuable compliance tools in one platform:
- Audits
- Established Processes
- Identity Verification
- Information Security
- Legal Contracts
- Monitoring
- Physical Security
- Regional Data
- Reporting
- Visitor Badges
Audit Reporting Tools
Be audit-ready in an instant. Digital workplace management systems automatically create and store an audit-proof paper trail. You can immediately recall this paper trail for any compliance and reporting needs.
You can choose a custom date range and variables from your visitor management dashboard to generate reports on-demand. The tool allows users to export data and signed documents to prepare for an audit at a moment’s notice.
Established Processes
iLobby ensures data protection with established processes and practices. System and Organization Controls (SOC) 2 provides uses third-party audits to meet the needs of a broad user base. SOC 2 reports ensure security, availability, and privacy processed by systems.
Identity Verification
Digital visitor management systems ease visitor identification. Check-in kiosks can capture visitor photos, run names against watchlists, and kiosk ID scanners even allow high-security workplaces to scan government-issued ID cards or passports to validate visitors.
Pre-registration solutions allow advance visitor validation, with guests completing sign-ins and submitting documents through their smartphones.
Information Security
Infosec (information security) involves practices to secure data from unauthorized access. Data can be vulnerable both in storage and during transmission, so it requires a multifaceted approach to mitigate risk. iLobby safeguards data with internal policies and processes.
Legal Contracts
Capture and store digital signatures for legal contracts onsite or through visitor pre-registration.
Empower the automation of liability waivers, policy agreements, NDAs, and other legal documents. DocuSign integrations, for instance, allow for automated version control, tracking, notifications, and reminders.
Quickly create, share, and sign legal documents in one location.
Monitoring
It is essential to monitor and track guests to achieve visitor-compliance goals. A real-time dashboard allows for monitoring multiple locations from one centrally managed platform. A glance gives an accessible overview of who is currently in the building for streamlining communications, emergency and evacuation notification, and security and safety purposes.
Set custom permission levels, such as Admin, Security, and Employee level access. So data is only accessible to those who need it most.
Physical Security
Access control integrations monitor and automate physical access to your building. You remotely control door, gate, and turnstile access by bundling hardware and software solutions. Preset conditions and watchlists ease compliance, automatically identifying and denying entry to flagged individuals.
ITAR-compliant organizations, for instance, can use their visitor management system to screen visitors against terrorist and no-fly lists or against custom watchlists.
Regional Data
Staying compliant with regional standards and regulations is challenging, especially for organizations with multiple or changing worksites. The legal documents you must collect from visitors and regional regulations vary between countries, states, and regions.
Multi-location organizations benefit from the combination of hardware-software visitor management platforms. At iLobby, we send out a sign-in kiosk preloaded with our software for a simple, turnkey solution. iLobby implements a flow based on your unique customer needs.
Reporting
Automated reporting tools generate custom reports from all locations in one place. End-of-day reports can be sent to security officers with filters to sort and discover important data. You can create compliance-friendly reports for any industry with unlimited secure storage and custom features like real-time updates, emergency updates, and watchlist alerts.
Secure access and data encryption keep reports compliant with data governance requirements.
Visitor Badges
Any workplace can take advantage of the benefits of visitor badges. Printing badges onsite allows security teams to identify everyone in your building visually. In a single glance, they can see who has completed sign-ins.
Visitor badges can include key identifying information and purpose of visit to establish who each visitor is and what areas they can access. It also ensures that all guests have completed the sign-in process. For example, a contractor can only print off their contractor badge once they have completed sign-in, which may include:
 Verifying their ID
Verifying their ID
 Signing necessary documents
Signing necessary documents
 Providing any required certifications
Providing any required certifications
This protects your facility from compliance and liability challenges.
Using color-coded badges further improves visual identification. Security officers can immediately see each person’s role and security access.
What is Data Governance
A facility management system collects important data from individuals and your organization. Every organization needs a data governance process to protect and use that data effectively. In effect, data governance refers to how your organization manages the data it collects, stores, or shares.
Having a sound data governance program improves your data’s overall security, quality, and usability. The program is also essential to data-centric compliance regulations like GDPR.
A governance program should consider the people, processes, and technology in your building to manage your data:
- Accountability
- Availability
- Collection
- Compliance
- Integrity
- Organization
- Performance
- Quality
- Security
- Stewardship
- Transparency
- Usability

Visitor Management Compliance Regulations
Common compliance standards for data security and facility monitoring are prebuilt into top visitor management systems. Depending on your region, industry, and facility, you may require additional customization to meet compliance standards. Industry-leading facility management providers, like iLobby, offer additional customization options to adhere to any compliance regulations your need.

Disclaimer: This overview is meant as a primer and is not legal advice. Here is a quick overview of common compliance regulations:
 CCPA Compliance
CCPA Compliance
The California Consumer Privacy Act (CCPA) is designed to protect the rights of consumers regarding how businesses collect, store, or share their data. CCPA regulations are similar to GDPR, although their application is more specific, focusing on ‘natural persons’ from California.
A business must be capable of providing all data they have stored of a customer on demand to be CCPA compliant. They must also be capable of providing a list of other parties with whom they have shared that information. Data covered by CCPA regulations includes (but is not limited to):
- Address
- Driver’s License & ID
- IP Address
- Location
- Names
- Personal Information (ex., Religion, politics, sexual orientation/identity)
- Search & Browsing History
- Social Security Numbers
If a business fails to follow privacy guidelines or provide consumers with the requested information, the consumer can sue them. They are also open to class action lawsuits. A breach is unnecessary to sue for failing to adhere to privacy guidelines.
In addition to consumers suing, failures in CCPA compliance can also result in fines from regulators. Once notified of a violation, a business has 30 days to comply or face fines of up to $7,500 per record. Organizations may have thousands or even millions of records, so fines can quickly add to massive proportions.
Does my Organization Have to be Compliant with CCPA?
The first step in CCPA compliance is understanding if it is relevant to your organization. It is important to remember that a business doesn’t have to be in California for CCPA regulations to apply. Any company that serves or collects data from California residents must comply if they:
- Have annual revenue of at least $25 million
- Collect over 50% of their revenue from selling personal data
- Has personal data on 50,000 or more people
Any business that meets one or more of those three criteria while serving California residents must be CCPA compliant.
For more details, review the Office of the Attorney General’s official resource.
 C-TPAT Compliance
C-TPAT Compliance
Participation in Customs-Trade Partnership Against Terrorism (C-TPAT) compliance is voluntary. Although it isn’t a requirement, following C-TPAT requirements benefits organizations involved in the international supply chain.
C-TPAT-compliant organizations enjoy close cooperation with US Customs. A better relationship with Customs expedites all international shipping with:
- FAST lane border access
- Faster processing at Customs
- Fewer inspections
- Shorter border wait times
- Shorter supply chains
- Reduced selection rates and exclusions
Voluntary C-TPAT compliance makes international trade more profitable for importers and exporters by reducing delays and increasing processing at the border. It is especially valuable for organizations transporting secure cargo, especially where terrorism is a concern.
What is C-TPAT Compliance?
The highest level of cargo security, C-TPAT, is a public-private sector partnership. Compliant organizations must meet specific data and physical security criteria, as well as access control processes. The program aims to improve border security and secure international supply chains.
Although the focus of C-TPAT regulations is on the US border, it is not limited to American organizations. Any business that is a stakeholder in the international supply chain can apply. This includes importers, carriers, consolidators, liquidators, customs brokers, and manufacturers.
Understanding the minimum security criteria for your organization’s role in the supply chain is essential. Leveraging visitor management software can help achieve C-TPAT security requirements. For example, ensuring guests sign NDAs, enforcing watchlists, and ID verification.
For more details on minimum security criteria, consult US Customs and Border Protection.
 FISMA Compliance
FISMA Compliance
The Federal Information Security Management Act (FISMA) brings information security to US national security interests. The Act regulates guidelines and standards that reduce security risks to federal data. FISMA compliance involves the planning, documentation, processes, and implementation of information security programs for all applicable organizations.
FISMA Requirements
Agencies and contractors must use a secure framework that protects government assets and information to meet compliance requirements. Accomplishing this requires following specific guidelines, which include:
- Conducting ongoing monitoring and risk assessments
- Implementing security controls and a risk management program
- Maintaining and categorizing inventory of information systems and risk levels
- Maintaining certifications and accreditations
- Preventing unauthorized access, use, or alteration of information
- Protecting the integrity, availability, and confidentiality of all sensitive data
The primary target of FISMA compliance is Federal agencies. However, some public organizations must also be FISMA compliant if they have certain relationships with government agencies. For example;
- Provide services to government agencies
- Support Federal programs
- Are supported by Federal programs (i.e.., receiving grant money)
Two regulatory bodies support FISMA.
- The National Institute of Technology (NIST) creates risk management and IT security programs.
- The Department of Homeland Security (DHS) implements NIST programs for FISMA systems.
Review the Act with the Library of Congress.
 FSMA Compliance
FSMA Compliance
A well-regulated food supply chain prevents contamination and is necessary for businesses and consumers. Food supply regulations protect individuals’ health and safety, decrease the need for recalls, and reduce product issues. This is the role that FDA Food Safety Modernization Act (FSMA) compliance plays in the supply chain.
FSMA and food safety systems address activities at different points of the global supply chain, regulating food supply processes. Regulations control the importation, growing, harvesting, and processing of food in the US. FSMA compliance takes proactive measures, preventing illness and contamination rather than responding to it. This approach saves businesses and governments time and money while protecting public health.
Although FSMA compliance is US-centric, voluntary compliance programs benefit organizations that want to do business involving the US food supply.
Seven Rules of FSMA Compliance
Each industry and step in food supply and safety systems has set rules and regulations under FSMA. The complete list of FDA rules and guidance includes 88 total entries to date. Organizations must understand which rules and guidelines apply specifically to them. However, these seven rules of FSMA compliance serve as an excellent jumping-off point for food and beverage organizations.
- Accredited Certification: FSMA-compliant organizations require certification from accredited third-party bodies. Third parties conduct safety audits to evaluate, monitor and submit assessments to the FDA.
- Foreign Supplier Verification (FSVP): The FSVP is required for foreign suppliers to reduce health hazards. It involves planning to analyze, monitor, and control hazards, protection from adulteration, and declaring food allergens.
- Intentional Adulteration: Protection against intentional adulteration is a component of the Food Defense Plan. It involves identifying vulnerable processing steps, preventative measures, monitoring, corrective measures, training, and record-keeping.
- Preventative Controls: The preventative control rule has expanded to include human and animal food products. All producers require a hazard analysis plan and preventive controls. Additionally, producers require plans for oversight, supply chain control, and product recalls.
- Produce Safety: The produce safety rule applies to growing fruits and vegetables for human consumption. It involves microbiological counts and testing, water testing, animal standards, training, and equipment and food handling safety standards.
- Sanitary Transportation: Transportation has several potential vulnerabilities for food safety, such as temperature maintenance and vehicle condition. The Sanitary Transportation Rule applies to logistic organizations and receivers of food and beverage products. Standards include vehicle design and maintenance, controlled conditions, training, and record-keeping.
- Voluntary Qualified Importer Program (VQIP): Foreign food producers and organizations can volunteer for the VQIP program. Although participation requires a fee, it saves time and money by expediting the inspection and evaluation of products entering the US food supply chain.
FSMA food and safety systems rely on sophisticated technology to meet its stringent regulations. Learn more about FSMA compliance software and the updated traceability requirements.
 GDPR Compliance
GDPR Compliance
General Data Protection Regulation (GDPR) compliance defines how organizations collect, store, use, and own data. It is similar to CCPA compliance’s focus on consumer and personal data. However, its application is even more widespread and stringent.
GDPR applies to all companies that collect, store, or use the personal data of European Union citizens. This can be as simple as storing cookies from websites or more involved such as collecting visitor data on a facility sign-in kiosk.
How to be GDPR Compliant
EU citizens have more rights over their personal data through the GDPR. To meet these rights, organizations must provide individuals with access to their data. Individuals must also be able to correct, wipe, or object to processing their data.
In addition to personal data rights, GDPR compliance also dictates how organizations protect data, report breaches, and controls training and transparency policies. Non-compliance results in significant fines and damages an organization’s public reputation.
If you conduct business globally or involving EU citizens, you must follow the GDPR Compliance Checklist.

Transparent Data Collection

Understand Your Data

Data Evaluation

Create Data Register

Determine Supervisores

Privacy Policy
Risk Assessment

Education
 GLBA & FMA Compliance
GLBA & FMA Compliance
Financial products and services are responsible for safeguarding, handling, and sharing sensitive data. The Gramm-Leach Bliley Act (GLBA) and Financial Modernization Act (FMA) support the goal of ensuring information security and confidentiality.
By protecting consumer records, GLBA compliance builds trust and reliability. These consumer features are a valuable ‘carrot’ for financial institutions, in contrast with the ‘stick’ of non-compliance penalties. Failure to comply with GLBA includes:
- Fines up to $100,000 per violation.
- Revoking licenses.
- Up to five years imprisonment.
In short, GLBA compliance is beneficial, while non-compliance results in harsh penalization.
Guiding Rules of GLBA
Following GLBA regulations and standards involves multiple steps. Organizations must undergo specific precautions and plans around collecting, using, and sharing consumer information. However, the basics of GLBA compliance follow two primary rules.
- Privacy: The privacy rule ensures that financial institutions and related services provide all consumers with adequate privacy notices. Notices cover the information collected, its use and sharing, and how the organization protects that data. Additionally, the consumer should receive instructions on how to opt out of having data shared with third parties. You must provide privacy notices as soon as the consumer relationship is established and follow up annually.
- Safeguards: The safeguards rule establishes how organizations protect data through security protocols and safeguards. This involves both physical and digital security measures. As well this rule requires that all breaches are communicated to affected customers.
Learn more about GLBA through the Federal Trade Commission.
 GMP Compliance
GMP Compliance
Workplaces must establish Good Manufacturing Practice (GMP) compliance to ensure consistent quality of manufactured goods. The FDA puts good manufacturing practices into effect to protect consumers from contaminated, ineffective, and hazardous products.
GMP compliance establishes practices for manufacturers, packagers, and processors of:
- Drug
- Medical Devices
- Certain foods
- Blood
The regulations allow organizations significant decision-making in how they implement controls. However, this flexibility is tempered by strong legal enforcement of GMP-compliant manufacturing. Failure to meet compliance requirements can lead to costly product recalls. As well, non-compliant organizations are liable to face fines, jail time, and seizures. Individuals, like doctors, who do not follow GMP regulations may also face lawsuits and have their licenses revoked.
Essentials of GMP-Compliant Manufacturing
Good manufacturing practices fall broadly under five principles. These are known as the Five P’s of GMP.
- People: People must have clear roles and responsibilities, follow all procedures, and have the proper training.
- Procedures: Document and record all procedures, investigate and report abnormalities, and cover critical processes.
- Products: Follow specifications for products at all stages, from raw materials to finished products. Research, sampling, developments, testing, controls, and recording must use repeatable methods.
- Premises: All premises and equipment must be validated and calibrated, have proper procedures, schedules, and records, take measures to avoid cross-contamination, and be designed for effective cleaning.
- Processes: Identify, define, and document all critical steps. Ensure effective controls are in place.
Explore how to streamline health and safety in food manufacturing to meet on-premises and standard operating procedure requirements with iLobby.
For current good manufacturing practices regulations, consult the US Food & Drug Administration.
 ITAR Compliance
ITAR Compliance
Organizations that offer products or services related to US defense and military technologies must be International Traffic in Arms Regulations (ITAR) compliant. The information that ITAR compliance protects is highly secure and directly relates to national security. As such, regulations are strict, and non-compliance penalties are significant.
Organizations that fail to adhere to ITAR compliance requirements may face fines of up to $1,000,000 per violation and/or ten years imprisonment. To ensure your organization avoids these penalties, consult the ITAR Compliance Checklist.
The Impact of ITAR Compliance
Facility management tools automate visitor screening, helping to ease compliance. ITAR-compliance secures processes and facilities to:
- Protect critical military technologies
- Prevent unauthorized access with deny lists and watchlist screening
- Create a formal process for visitor monitoring
- Working with foreign organizations in the supply chain (monitoring, screening, documentation)
Consult the US Department of State for more details on ITAR regulations and who needs to participate.
 PCI DSS Compliance
PCI DSS Compliance
information. Payment Card Industry Data Security Standards (PCI DSS) establish and maintain secure environments for payment card data. PCI DSS compliance applies to every company that accepts, stores, processes, or sends payment card information.
There is no exemption for PCI DSS compliance for small businesses. The standards are not limited to online activity and include activities that accept credit card information over the phone.
PCI Compliance is broken into four levels depending on the number of transactions processed:
- Six million transactions/year.
- 1 million to 6 million transactions per year
- 20,000 to 1 million e-commerce transactions per year
- <20,000 e-commerce transactions per year; or up to 1 million non-email transactions per year
Merchant levels dictate which Compliance Report or Self-Assessments Questionnaire (SAQ) applies to your organization.
PCI DSS aids in safeguarding your organization from data breaches and cyberattacks that can lead to major costs and complications. Compliance also protects your organization from penalization in the event of a breach. Fines can reach up to $500,000 on top of expenses you incur addressing and resolving the breach.
For more details, review the complete PCI DSS compliance guide from the PCI Security Standards Council.
 SOC 2 Type 2
SOC 2 Type 2
Service Organization Controls (SOC) address the five trust service principles of information security.
- Security
- Availability
- Confidentiality
- Processing Integrity
- Privacy
SOC 2 Type 2 is the highest level of security certification for organizations that store customer data online. Certification for SOC 2 compliance indicates that an organization lives up to strict guidelines involving security procedures and policies and monitoring and risk prevention activities. SOC 2-compliant organizations earn trust for using top-level safeguards to protect confidential, private, and sensitive information.
How to Get SOC 2 Compliance
Earning SOC 2 certification is a lengthy process but a worthwhile one. It takes over six months to build a SOC 2 report, usually lasting for a year or more. How long report generation takes depends on an organization’s size, security infrastructure, and users. Getting SOC 2 compliance requires an audit focusing on a long-term analysis of your security program. Basic steps include:
- Assigning third-party auditors
- Creating a compliance roadmap
- Conducting an audit
- Obtaining certification and re-certification
Learn more about SOC types 1, 2, and 3 from the American Institute of Certified Public Accountants.

Assess Compliance & Data Governance Needs for Your Facility Management System
iLobby recognizes that every business, workplace, and manager is unique. Checking off boxes isn’t enough to ensure you get the right features for your workplace. Our team puts the customer first to determine how we can customize our product to optimize your facility’s processes and compliance requirements.
Book a demo today to assess your workplace’s compliance and data governance needs.